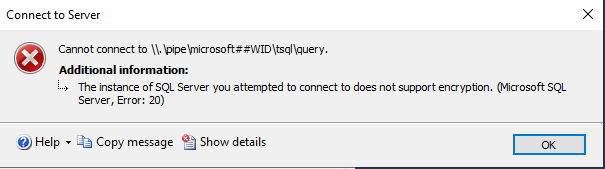
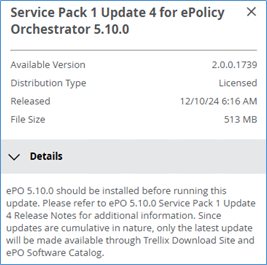
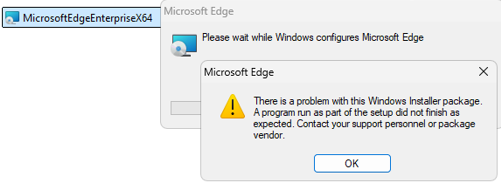
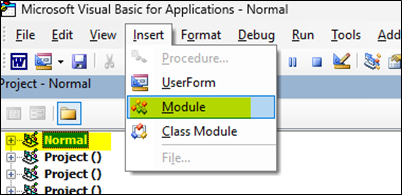
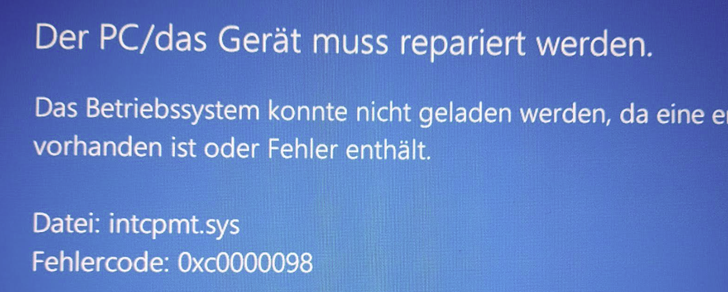
M365/Exchange Hybrid OAuth Testing command, OAuth-Cert out-of-sync 4001, IIS VDIR OAuth wrong
www.butsch.ch Resolve and find OAuth problem in Exchange Hybrid Setup Environment Short Understanding OAuth: OAuth (Open Authorization) is an industry-standard protocol that enables secure authorization for third-party applications without the need to disclose user credentials. It allows users to grant limited access to their resources on one site to another site, without sharing their credentials. […]